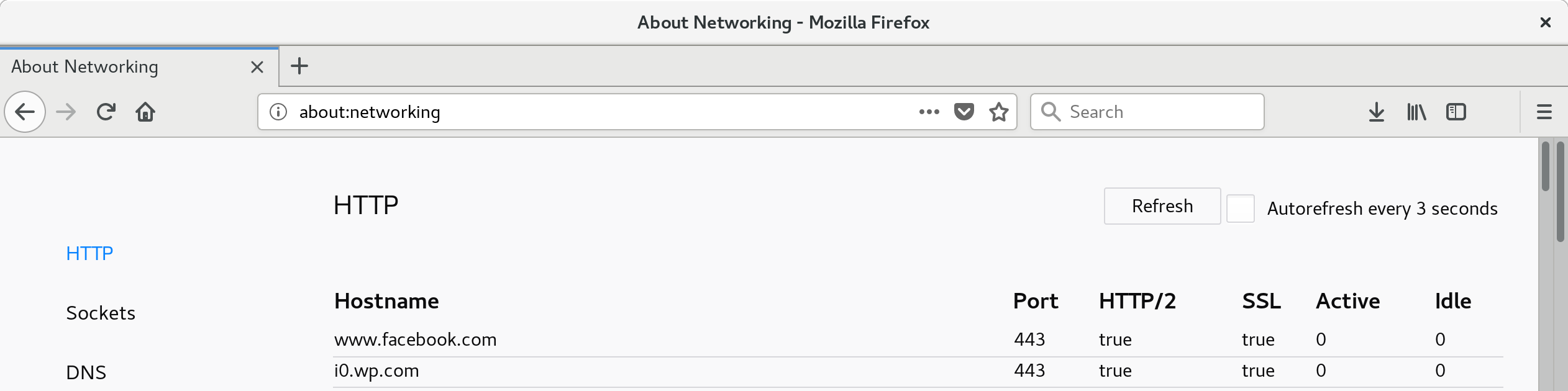
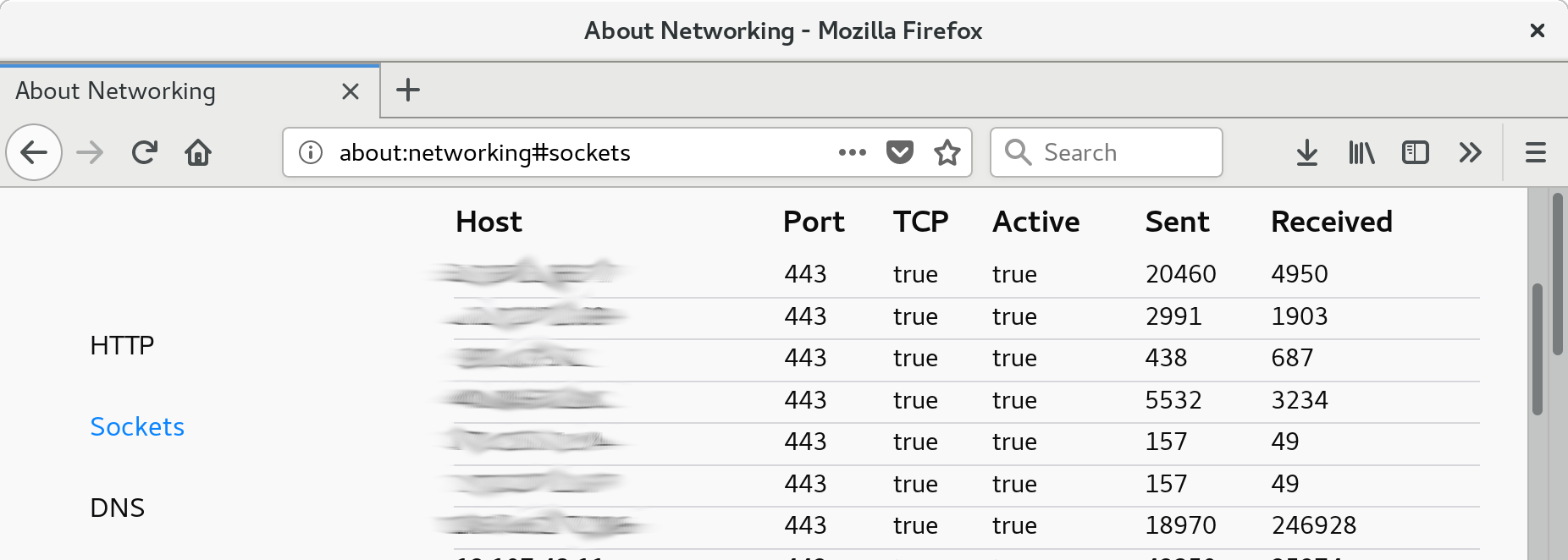
In firefox release 52 (Mar 2017), a new feature was added, about:networking . This local-only accessible URL permits the user to see the currently established HTTP connections
As well as the underlying TCP connection (including server IP address).
Now that firefox exposes the active connections that it knows about, I might be able to create a tool I have thought up:
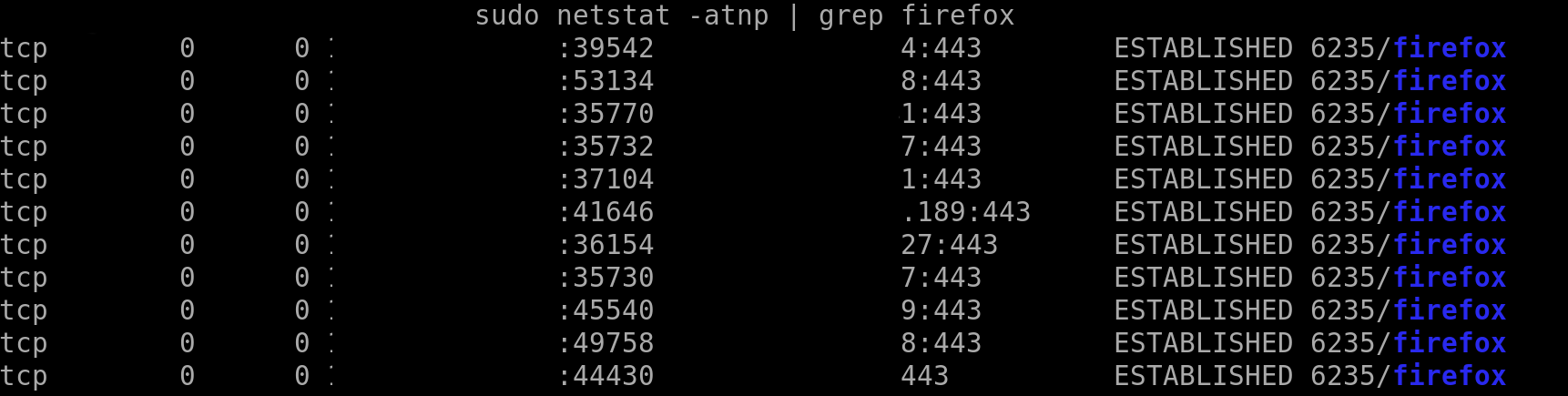
One performing analysis of a system to determine whether or not it is compromised (malware, otherwise connected intruder, etc…) might use the tool netstat (or its new replacement, ss) to answer the question of what network connections (ie, TCP sockets) are currently active and from which program.
The following screenshot shows a query using this tool to determine according to the OS what TCP sockets are established from firefox.
The idea behind my tool is that some malware may inject code into a web browser to piggy-back on the legitimate use-case that a browser would have reason to have active internet connections. This imagined tool would query Firefox for the connections it knows about and query the OS for the same, and thus perform a comparison. Most likely, malicious code injected into the browser would not properly populate the database that Firefox uses to report its legitimate connections. Those connections that show up in netstat but not from the Firefox report would be suspicious.
Current approaches:
- Use Greasemonkey or the likes to parse the about:networking and write to disk. This approach does not appear to have legs as Greasemonkey is unable to access the useful about: pages.
- Another approach is to use the Network logging function of the about:networking and write a parser for the logs. I don’t prefer this option, but may explore it.
Ideally firefox would offer an API accessible method to retrieve this information. Maybe there is another way to get this done, for now this project is just a thought.
One can read more about the about_protocol from Mozilla.